
An ongoing cyber espionage and surveillance campaign of an APT Group, SharpPanda, was discovered and identified to be targeting Southeast Asian government with a newly deployed backdoor malware. The malware was said to be developed, tested, and deployed over the past three years in order to compromise systems of a Southeast Asian government’s Ministry of Foreign Affairs.
______________________________
A. Nature of the Attack
The APT group initially compromise the target organization’s employees by sending spear phishing emails impersonating other government-related entities. The email contains malicious attachments that are weaponized copies of legitimate looking official documents and are used for the next stage of attack. The group then uses Royal Road, an RTF weaponizer, to exploit known vulnerabilities in Microsoft Word’s Equation Editor to deploy shellcode and deliver the backdoor payload.
______________________________
B. Malware Capabilities
Capabilities of the backdoor payload:
- Stealing and exfiltration of victim’s machine information
- Perform unauthorized actions on victim’s machine
- Registry enumeration
- Process creation and termination
- Running processes and services monitoring
- Monitor user’s actions
- File Modification
- TCP/UDP port enumeration
______________________________
C. Indicators of Compromise (IoC)
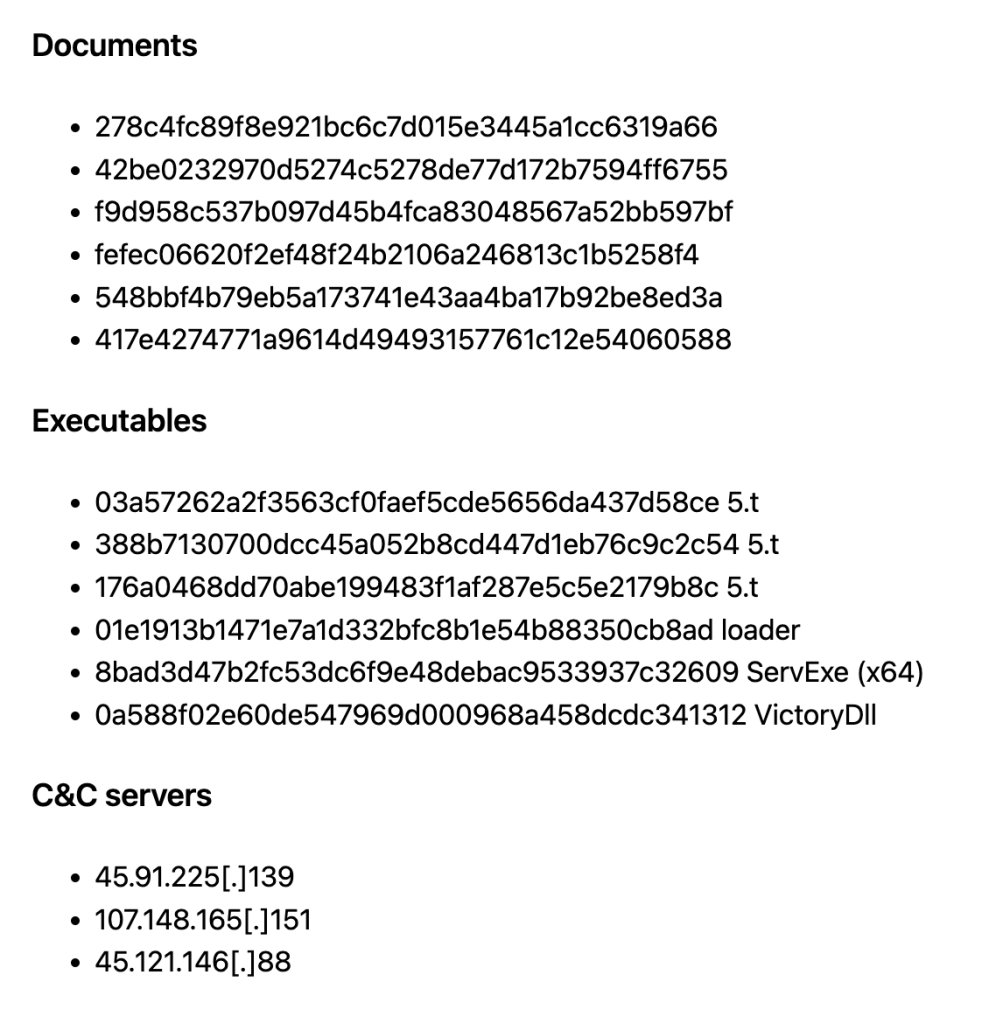
______________________________
D. Conclusion
In conclusion, organizations and businesses, both private and public, are highly advised to closely monitor and observe all assets for any indicators of suspicious/malicious activities. It is also highly recommended to implement relevant IOCs, YARA and Snort rules within the organizational security systems. In addition, providing and capacitate employees with cybersecurity knowledge and information to minimize attack surface.
