An Advanced Persistent Threat (APT) Group, dubbed as LuminousMoth, was observed to be conducting a large-scale campaign targeting government entities and organizations from South East Asian countries, including Myanmar and the Philippines. The APT group is also associated with a known Chinese-speaking threat group, HoneyMyte/Mustang Panda, which was attributed to malicious campaigns targeting local high profile government organizations of Asian and African countries.
In the recent ongoing cyber espionage campaign, which was dated back to October 2020, the threat group was seen to be using spear phishing emails to allow their malware to infiltrate victim’s machines that will ultimately lead to sensitive information being exfiltrated to the attacker-controlled infrastructure.
______________________________
A. Nature of Attack
Description of the attack:
The threat group was identified to be spreading malicious emails containing a Dropbox download link, which will download an archive file masquerading as a Word document. The RAR file contains malicious executable and DLLs files, wherein if executed will infect user’s system to gain persistence and foothold via auto-start techniques and deployment of Cobalt Strike’s beacon.
The malware will then try to check for available removable USB and external drives to propagate outside the victim’s machine by hiding the content of the drives and putting an executable file in its content. If a user clicks and runs the executable file, the malware will also infect the user’s machine and will try to propagate to other USB and external drives, thus continuously infecting users from the organization.
Additionally, the malware will drop two additional malicious files that will serve as its gathering and exfiltration mechanism. First is the use of an executable file that grabs a copy of files with specific extensions on a list of directories to a malware-created directory, along with the file’s metadata. The stolen files will then be archived and exfiltrated to the malware’s command-and-control. Second is a file dedicated to stealing cookies from the victim’s Chrome browser, which are used by Google for user authentication. Once stolen, these cookies can then be used by threat actors to hijack and impersonate the Gmail sessions of the victim.
______________________________
B. Actions to be Taken
CERT-PH recommends the following actions be taken:
- Check systems and devices for known vulnerabilities, and if applicable, apply the necessary patches and updates to mitigate security threats.
- It is highly advised to check for any indicators of compromise, such as suspicious files and unusual external communication. (Please see details below for reference.)
- Proactively monitor and secure systems and devices for any suspicious/malicious activities.
- Secure and ensure backups of critical data are always available and can be deployed, if an incident will occur.
- Provide employees with ample knowledge and training with regards to good cyber hygiene practices
______________________________
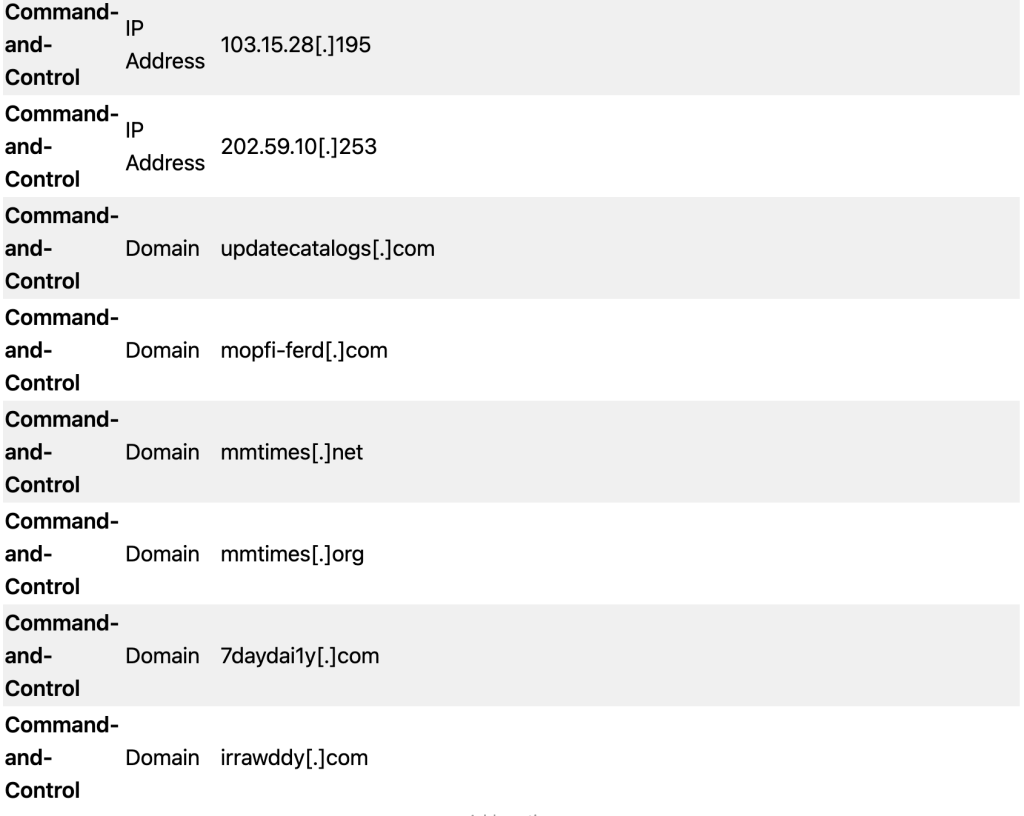
C. List of Indicators of Compromise (IOC)
| Item Type | Indicator Type | Indication value |
| Malware | Sha256 | 59b8167afba63b9b4fa4369e6664f274c4e2760a4e2ae4ee12d43c07c9655e0f |
| Malware | Sha256 | a934ae0274dc1fc9763f7aa51c3a2ce1a52270a47dcdd80bd5b9afbc3a23c82b |
| Malware | Sha256 | 869e7da2357c673dab14e9a64fb69691002af5b39368e6d1a3d7fda242797622 |
| Malware | Sha256 | 857c676102ea5dda05899d4e386340f6e7517be2d2623437582acbe0d46b19d2 |
| Malware | Sha256 | 1ec88831b67e3f0d41057ba38ccca707cb508fe63d39116a02b7080384ed0303 |
| Malware | Sha256 | 95bcc8c3d9d23289b4ff284cb685b741fe92949be35c69c1faa3a3846f1ab947 |
| Malware | Sha256 | 4a4b976991112b47b6a3d6ce19cc1c4f89984635ed16aea9f88275805b005461 |
| Malware | Sha256 | d8de88e518460ee7ffdffaa4599ccc415e105fc318b36bc8fe998300ee5ad984 |
| Malware | Sha256 | cf757b243133feab2714bc0da534ba21cbcdde485fbda3d39fb20db3a6aa6dee |
| Malware | Sha256 | f27715b932fb83d44357dc7793470b28f6802c2dc47076e1bc539553a8bfa8e0 |
| Malware | Sha256 | 361ccc35f7ff405eb904910de126a5775de831b4229a4fdebfbacdd941ad3c56 |