Microsoft released a security fix to an elevation of privilege vulnerability in Win32K Kernel. The flaw can be used together with other browser exploits to escape sandboxes or achieve system privileges. In addition, the company identified that the vulnerability is under active exploitation by threat actors.
______________________________
A. Nature of the Vulnerability
The nature of the vulnerability is described as:
CVE-2021-40449
A Win32k Elevation of Privilege Vulnerability that could potentially allow an attacker escalation of privilege (EoP) that can be used together with other browser exploits to escape sandboxes or achieve system privileges. Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code on the affected system.
______________________________
B. List of Vulnerable Systems
Vulnerable Windows Version are as follows:
- Microsoft Windows Vista
- Microsoft Windows 7
- Microsoft Windows 8
- Microsoft Windows 8.1
- Microsoft Windows Server 2008
- Microsoft Windows Server 2008 R2
- Microsoft Windows Server 2012
- Microsoft Windows Server 2012 R2
- Microsoft Windows 10 (build 14393)
- Microsoft Windows Server 2016 (build 14393)
- Microsoft Windows 10 (build 17763)
- Microsoft Windows Server 2019 (build 17763)
______________________________
C. List of Vulnerable Systems
CERT-PH recommends the following actions be taken:
- Administrators are urged to test and apply the latest and stable version of Windows Version to mitigate from known security threats.
- Having a good backup of the system before patching is a good practice, in case there are anomalies and issues encountered.
- For additional information, kindly refer to the official Advisory of Kaspersky and Microsoft(https://securelist.com/mysterysnail-attacks-with-windows-zero-day/104509/ | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40449)
______________________________
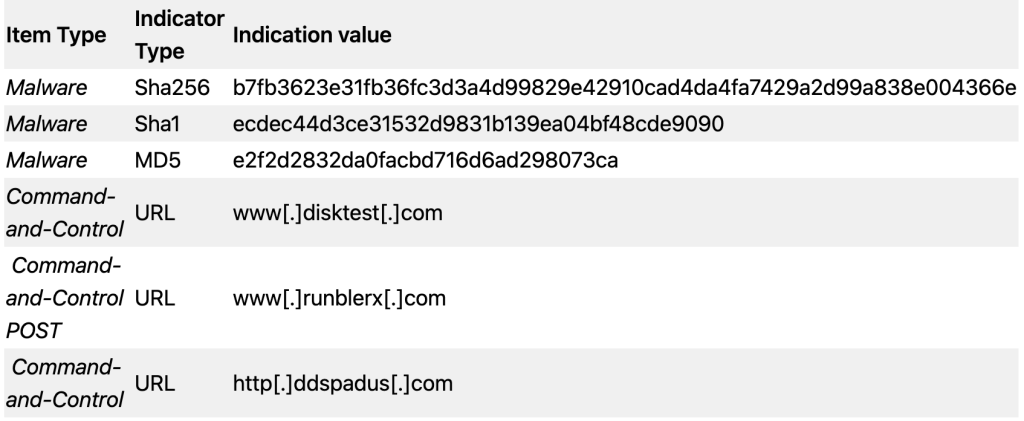
D. List of Indicators of Compromise (IOC)