An Advanced Persistent Threat (APT) Group dubbed as TA2722/Balikbayan Foxes was recently discovered impersonating as from DHL Philippines and Philippine Government entities including the Department of Health, the Philippine Overseas Employment Administration (POEA), and the Bureau of Customs, and the Manila embassy for the Kingdom of Saudi Arabia (KSA) targeting businesses from Shipping/Logistics Manufacturing, Business Services, Pharmaceutical, and Energy entities across the US, Europe, and Asia thru email phishing campaign.
______________________________
A. Nature of the Campaign
The threat group was identified to be spreading thru multiple threat distribution mechanisms using email phishing campaigns including:
- OneDrive URLs linking to RAR files with embedded UUE files
- PDF email attachment with an embedded OneDrive link or other malicious URL leading to compressed executables (.iso files) that download and run malware
- Compressed MS Excel documents containing macros which, if enabled, download malware
This email phishing campaign goal is to distribute Remcos and Nanocore Remote Access Trojan to gain access to the target’s computer and later to steal information to it.
______________________________
B. Actions to be Taken
CERT-PH recommends the following actions be taken:
- In conclusion, organizations and businesses, both private and public, are highly advised to do the following:
- Proactively monitor and secure identified systems and devices for any suspicious/malicious activities.
- Check systems and devices for known vulnerabilities, and if applicable, apply the necessary patches and updates to mitigate from security threats.
- Having an anti-virus software and/or host based detection tool is also recommended.
- Having a good backup of the system, in case there are anomalies and issues encountered to minimize, if not prevent the disruption of services.
- In addition, providing and capacitating employees with cybersecurity knowledge and information to minimize attack surface.
- For additional information, kindly refer to the official report of Proofpointl(https://www.proofpoint.com/us/blog/threat-insight/new-threat-actor-spoofs-philippine-government-covid-19-health-data-widespread)
______________________________
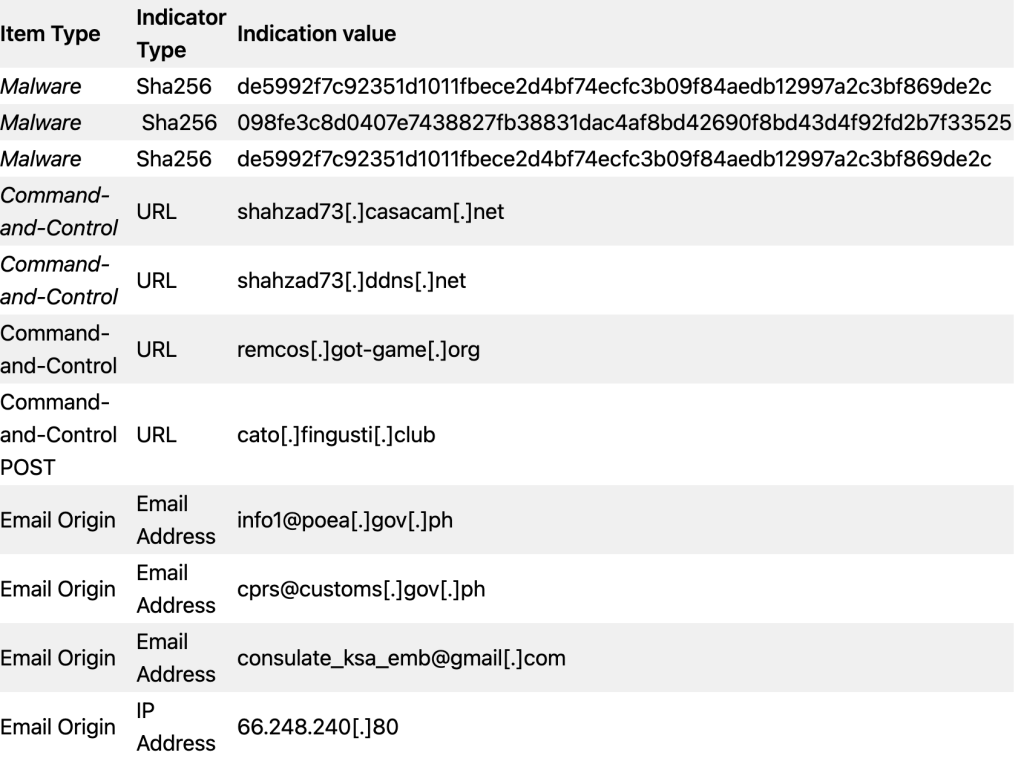
C. List of Indicators of Compromise (IOC)