A critical zero-day vulnerability in Apache Log4j2, a library used by millions for Java applications, that is being actively exploited in the wild was recently discovered that can allow a threat actor to gain system-level access to the vulnerable servers. Tracked as CVE-2021-42288, CERTS from different countries like New Zealand, Austria, and Germany have already spotted it being used by adversaries in the wild.
Apache is aware of the security vulnerability and already released the Apache Log4J v2.15.0 to address the issue.
A working proof of concept of this vulnerability was published on GitHub.
______________________________
A. Nature of the Vulnerabilities
The following vulnerabilities were described as:
CVE-2021-44228
A security vulnerability in Apache Log4j versions 2.0-beta9 to 2.14.1 has a CVSS score of 10.0. Logging untrusted or user-controlled data with a vulnerable version of Log4J may result in Remote Code Execution (RCE) against your application. This includes untrusted data included in logged errors such as exception traces, authentication failures, and other unexpected vectors of user-controlled input.
______________________________
B. List of Vulnerable Systems
Vulnerable Windows OS:
- All Log4J versions prior to v2.15.0 are affected by this specific issue.
______________________________
C. Actions to be Taken
CERT-PH recommends the following actions be taken:
- Test and apply the necessary patches for the packages/applications/systems/devices:
- Apache Log4j version 2.15.0
Note: For those who cannot upgrade to 2.15.0, in releases >=2.10, this behavior can be mitigated by setting either the system property log4j2.formatMsgNoLookups or the environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true. For releases >=2.7 and <=2.14.1, all PatternLayout patterns can be modified to specify the message converter as %m{nolookups} instead of just %m. For releases >=2.0-beta9 and <=2.10.0, the mitigation is to remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class.
- Proactively monitor and secure identified systems and devices for any suspicious/malicious activities.
- Having an anti-virus software and/or host-based detection tool is a must.
- Having a good backup of the system, in case there are anomalies and issues encountered to minimize, if not prevent the disruption of services.
- In addition, providing and capacitating employees with cybersecurity knowledge and information to minimize the attack surface.
- For additional information, kindly refer to the official report:
______________________________
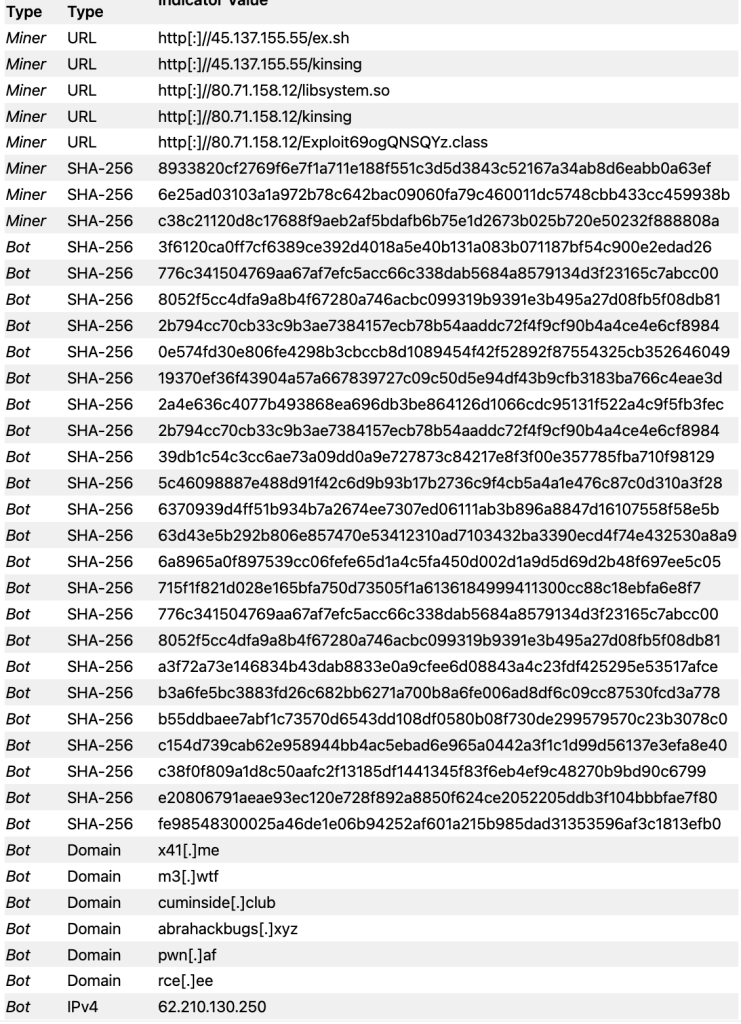
D. Indicator of Compromised (IOC)